Keeping company data safe is a top priority in a fast-paced…
What do you think of when you hear “access management”? Most people think of SSO (single sign-on) and stop there. While SSO is part of access management, it’s just a small part. Access management is also about securing your most important web resources. When your applications and your data are exposed to the internet, you are only as secure as your access management strategy. Additionally, the ability to allow your employees or your partners to securely access shared resources is another feature of access management.
Define your Access Management Strategy
Companies must define a clear access management strategy in order to both be secure and be positioned for future success and growth.
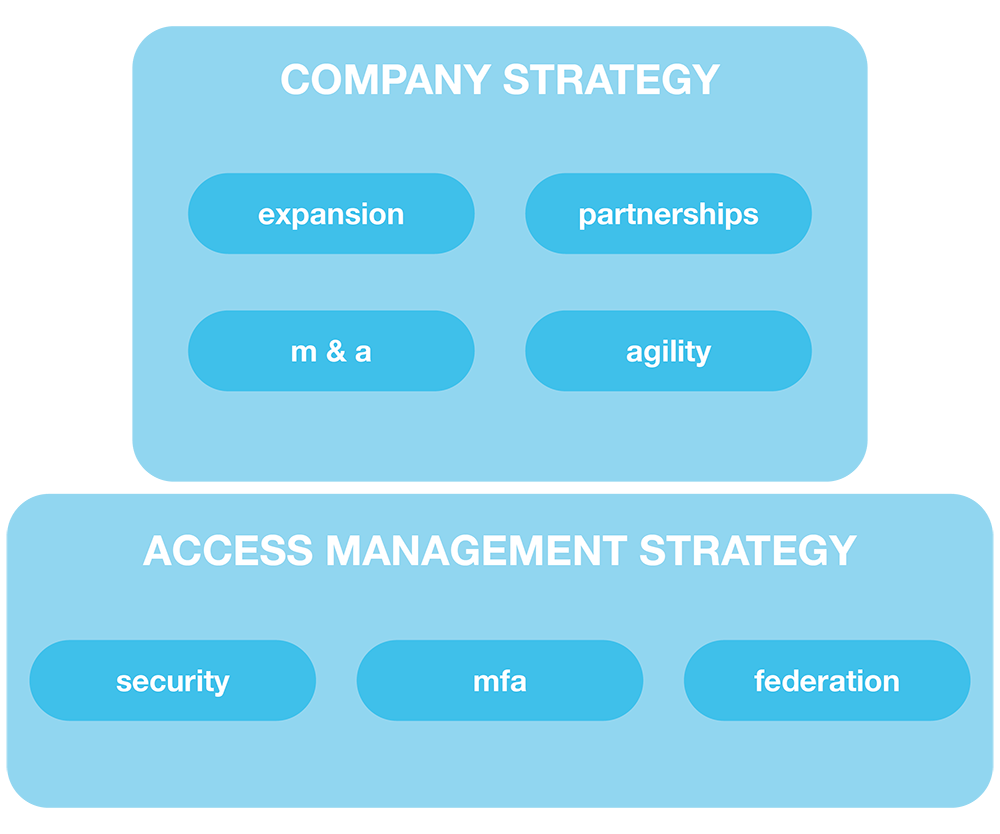
What is the long-term vision of the company?
Are you targeting partnerships, mergers, acquisitions? If you are, the ability to federate with those potential new users will allow for a seamless integration of the two entities.
Do your customers need the ability to securely access resources outside of your control? For example, because Google had a federation strategy, when they added YouTube TV using your existing Google account, they were immediately able to allow all of their subscribers to access YouTube TV content on any device like Apple TVs, Samsung Smart TVs, etc.
Proactive vs. Reactive. MFA (Multi-Factor Authentication: authenticating users based on more than just a password, like a “factor” they know), for example, is frequently being added to regulations like FINRA for additional users. Companies need to start proactively adding MFA to their entire user populations. Consumers are beginning to choose the companies with which they do business based on which ones have the strongest security stance.
What exactly is MFA?
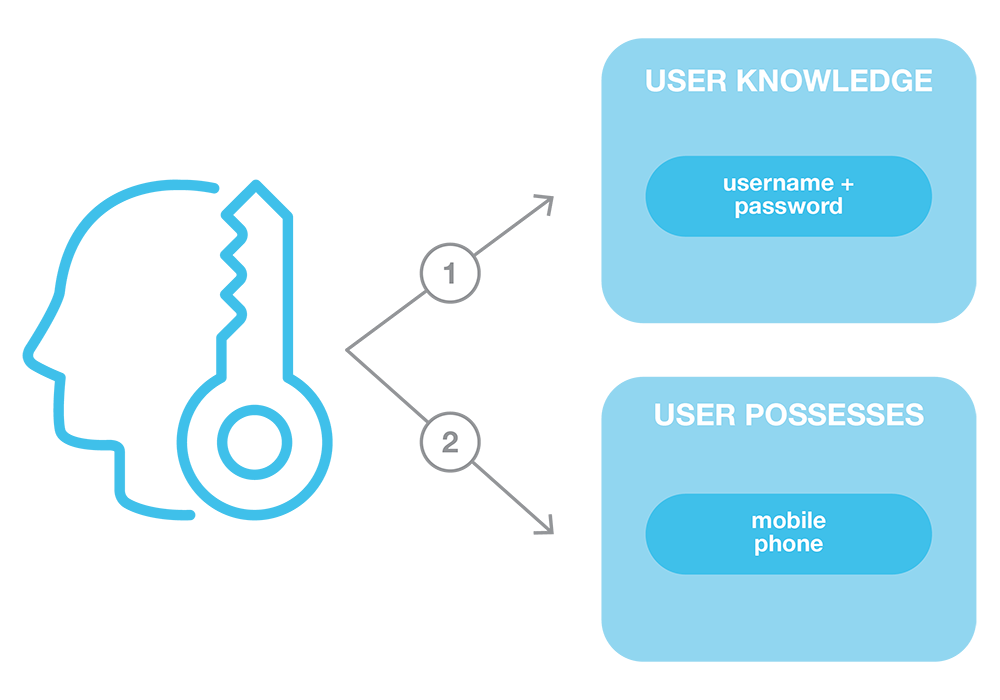
Multi-factor authentication is a key component of access management. A username and password combination is not enough, as it is only a single factor (what the user knows). A second factor (something the user has), like a mobile phone, is extremely important in authenticating users. A one-time password sent to a mobile phone or via a voicemail left on a land-line are the preferred options. Because email can be accessed in so many different ways, it’s typically not a reliable second factor because an email client can exist on any number of computers, and even new devices can be used to access that email account.
No more shared accounts! One of the big deterrents to MFA is that person A wants to share their account with person B, which means the chosen MFA solution cannot fully rely on something Person A has, such as a mobile phone. This should not be a reason to not use MFA, but instead should be a reason to create a separate login (username, password, MFA info that accesses the desired account information) for Person B.
Security over user convenience! Companies spend too much time trying to figure out how they are going to remember devices so users don’t have to enter their second factor every time they log in. Instead, companies need to realize that a password is never secure enough to solely rely on for access to their systems, and they should ALWAYS require a reliable second factor.
What is federation?
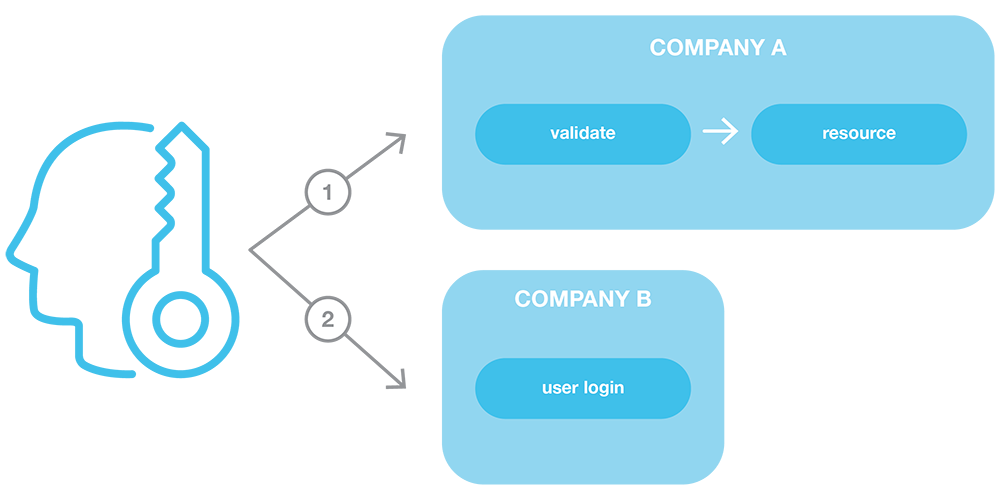
Federation 101: Simply put, federation is when a user is able to access Resource A owned by Company A using a username/password owned by Company B. For example, any time a user chooses to forego creating an account at a site and instead logs in with Facebook or Google, they are using a form of federation. Company A trusts Company B to authenticate the user, and then Company A simply allows the user to access Resource A.
Strategic benefits of federation. Federation allows companies to be agile and quickly and securely allow access to its resources to new users as well as allow its users access to resources controlled by other companies. This strategy can be used for both employees of the company and customers of the company depending on need.
What is web perimeter security?
Web Perimeter Security (WPS) is no longer optional; it is now required. WPS, simply put, is securing all your resources at the web server layer instead of at each application. This allows each protected application to “trust” that the traffic it is receiving has been properly authenticated and authorized by your access management solution and further limits the attack vectors available to a hacker. All traffic is funneled through these web servers, which are hardened both on a server level and web server level.
—
In conclusion, access management for your company must be more than just SSO and a way to simplify user experience through a single login to multiple applications. It must include:
- Alignment with company-wide vision
- Multi-factor authentication (MFA)
- Federation (SAML, OAuth, OpenID Connect)
- Web perimeter security
Zirous is an experienced strategic partner who understands how company needs and processes affect governance strategies, including access management. Reach out to learn how our partnerships like Oracle, SailPoint, and Okta can provide value to your organization.



This Post Has 0 Comments