Keeping company data safe is a top priority in a fast-paced…
“Sign-on” and “login” have grown by leaps and bounds since the phrases first came into use. They used to just refer to validating a username and a password before allowing a user to access protected/secured online content. It used to just involve a simple file containing those usernames and passwords.
But as technology has evolved, so have the meanings of these terms. Why should you care? Because if you don’t understand what it is today, you can greatly undervalue the systems and people who manage sign-on / login for you — whether that’s accessing work content like Office365, Salesforce, AWS, etc. or personal content like Gmail, YouTube, Netflix, etc. Undervaluing these systems and the people who manage them, or underestimating the importance of them, can put you or your business in harm’s way.
Today’s Username/Password Validation Systems
The systems involved today in collecting and validating username and password typically include:
- A load balancer,
- A web server,
- An application server, and
- An LDAP server
Depending on the high availability requirements, the load balancer can be involved at every layer as well!
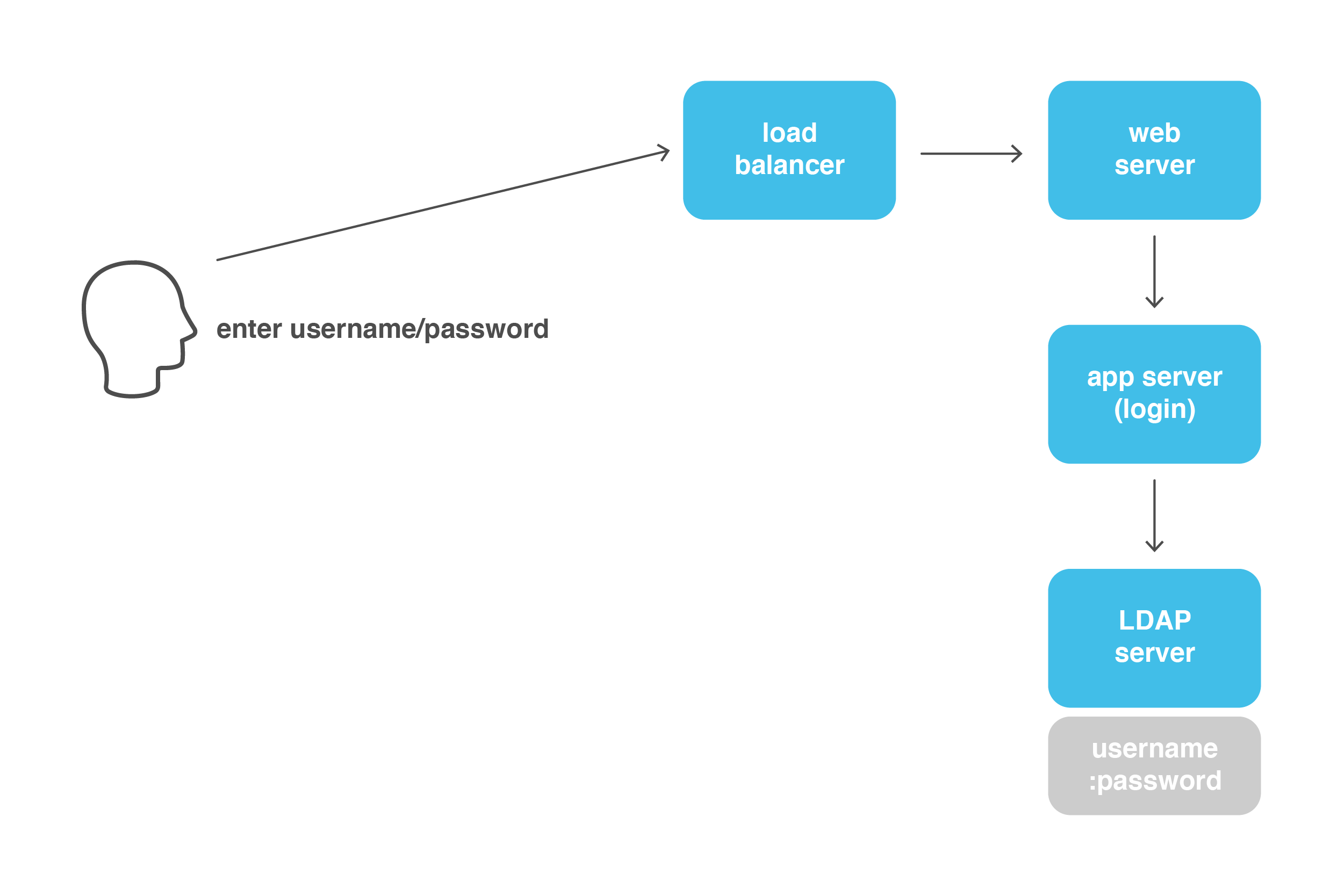 As you can see, a single username/password validation requires communication between four different systems instead of just the validation in one file on a single server. Additionally, most LDAP servers rely on some type of database to store the user’s password in a secure way.
As you can see, a single username/password validation requires communication between four different systems instead of just the validation in one file on a single server. Additionally, most LDAP servers rely on some type of database to store the user’s password in a secure way.
What if multi-factor authentication is involved?
Multi-factor authentication is an important piece of the access management puzzle, but it adds a layer of complexity to your login environment. (We talk about the value of MFA and more here.) Now we’re talking about interacting with a third-party service that will handle sending and receiving one-time use passwords to phones or email addresses as well as possibly validating a time-based one-time password (TOTP) so users can use authenticator applications like Google’s Authenticator or Okta’s Verify app.
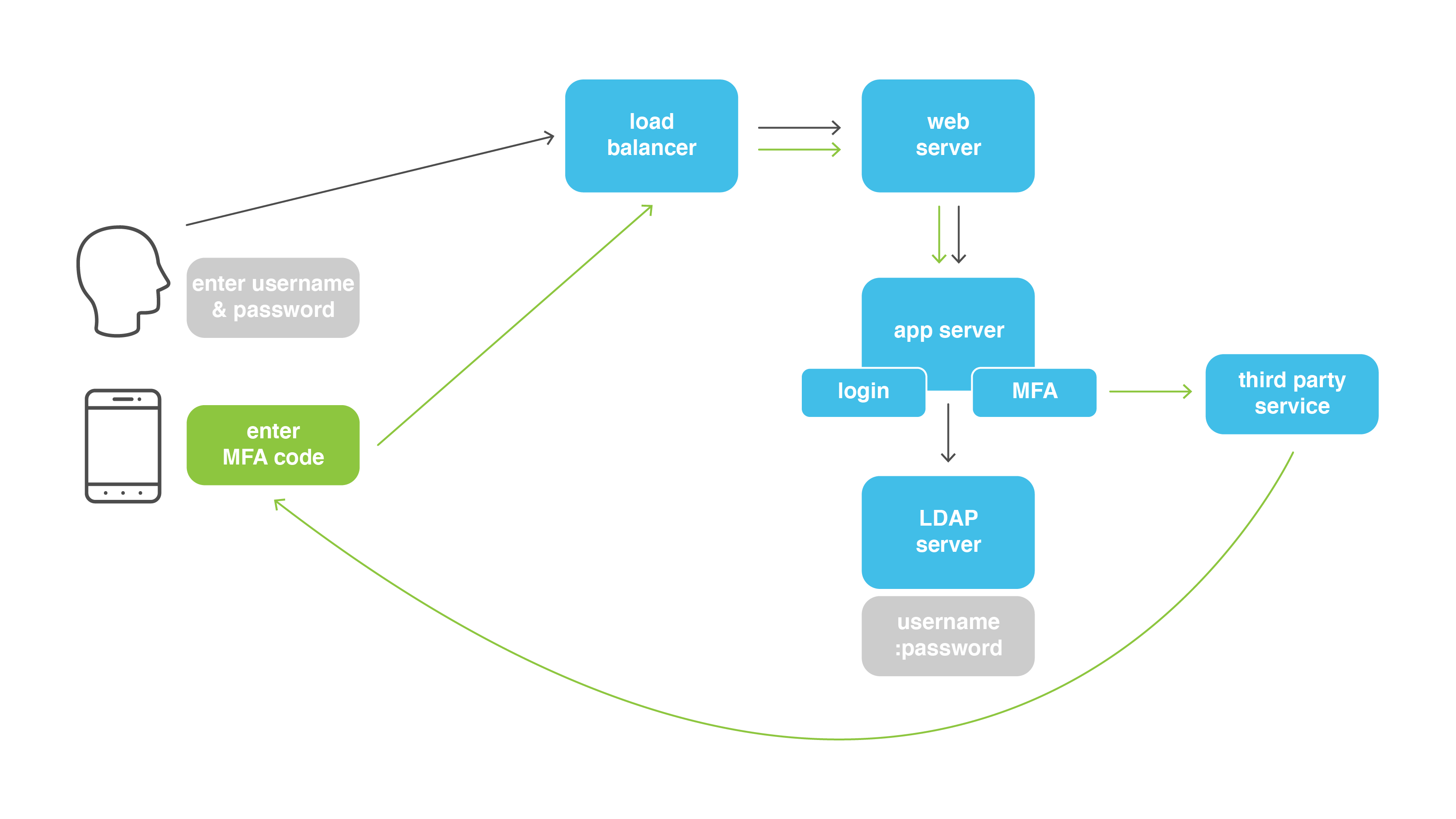 Now there are interactions among five different systems including either a PC or mobile phone for the OTP/MFA Code challenge.
Now there are interactions among five different systems including either a PC or mobile phone for the OTP/MFA Code challenge.
What if an enterprise-grade access management solution is used?
Now, depending on what the chosen solution is (Oracle’s Access Management or ForgeRock’s Access Management, among others), we are talking about adding at a minimum another application server and an LDAP server or database.
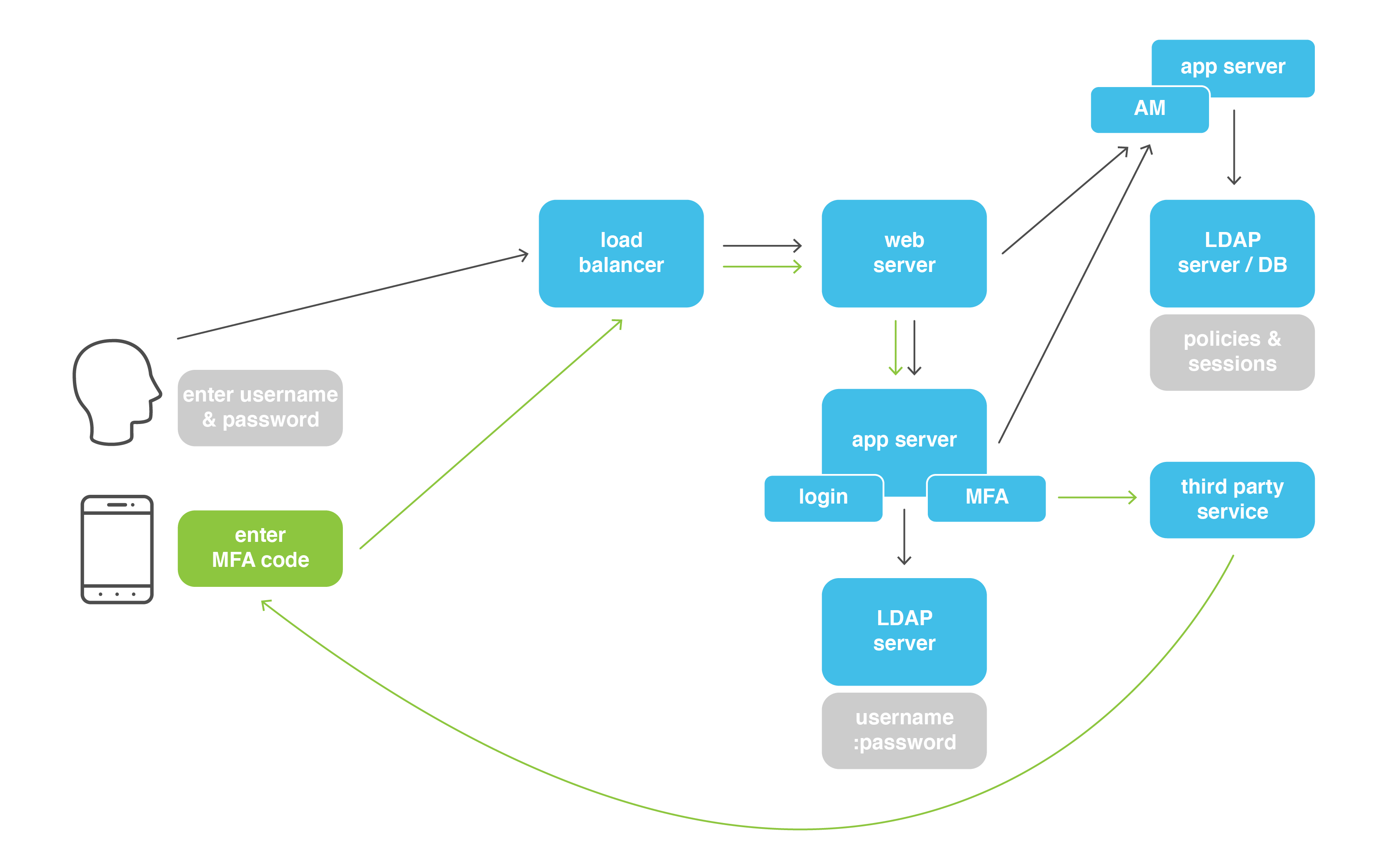 So, let’s count, that’s now LB + web server + application server 1 (login/MFA) + app server 2 (AM) + LDAP server (user info) + LDAP/DB (user sessions) + third-party MFA server = 7 different systems involved! That might be seven times the number expected if you were expecting one system to accomplish this. (Did we mention things are a little more complex now?)
So, let’s count, that’s now LB + web server + application server 1 (login/MFA) + app server 2 (AM) + LDAP server (user info) + LDAP/DB (user sessions) + third-party MFA server = 7 different systems involved! That might be seven times the number expected if you were expecting one system to accomplish this. (Did we mention things are a little more complex now?)
What about cloud?
When it comes to the cloud, any one or all of the systems depicted can be leveraged in the cloud. Companies like Okta have great cloud solutions with incredible uptime, but due to the complexities discussed above, there is still some downtime. For both on-prem and cloud solutions, there are typically multiple data centers involved which adds additional complexity!
What does it mean?
Hopefully, this information allows you to understand the complexity of the systems you’re using and appreciate when they work — and also understand when there are issues. If you’re a decision maker trying to determine how to bring this type of functionality to your company (and we strongly recommend that you do), Zirous can help with that! Finding the right solution is a daunting task, but we have your back. Our identity team holds decades of experience in all types of identity solutions, from full enterprise-wide implementations to single sign-on pieces. We can help you evaluate whether an on-prem or cloud is right for you, which systems you’ll need, and more, depending on your business processes and goals.



This Post Has 0 Comments